CyberArk and BeyondTrust are some of the best Identity and Access Management (IAM) and Privileged Access Management (PAM) solutions providers for businesses. CyberArk works by combining the use of Adaptive MFA, SSO, Lifecycle Management, Directory Services and User Behavior Analytics to protect the identities and critical assets of workforce users, privileged users and third-party vendors as they access sensitive data. BeyondTrust is well rooted in zero trust principles and works by offering an identity-first security approach that allows users to detect threats across their identity estate and respond by controlling privileges, credentials, access and secrets.
Both CyberArk and BeyondTrust are powerful, highly rated IAM and PAM systems trusted by many users, but which one should you choose?
This article compares the features, capabilities and pricing of the two solutions to help you make an informed decision on which one suits your needs.
CyberArk vs. BeyondTrust: Comparison
CyberArk and BeyondTrust are similar in many ways. The table below summarizes the important features available on the two platforms.
| Features | CyberArk | BeyondTrust |
|---|---|---|
| Security focus | Accounts | Assets |
| Password vault | Yes | Yes |
| Multi-factor authentication | Yes | Yes |
| Password management | Yes | Yes |
| Account management | Yes | Yes |
| Privileged access management | Yes | Yes |
| Threat detection | Yes | Yes |
| Free trial | Yes | Yes |
| Organization | Account | Host |
|
|
|
CyberArk and BeyondTrust pricing
Pricing for CyberArk and BeyondTrust is based on the specific solution you choose.
Quotes are only available by contacting their sales team.
Feature comparison: CyberArk vs. BeyondTrust
CyberArk and BeyondTrust offer many features geared toward secure identity management.
Password management
CyberArk offers workforce password management solutions that securely store, manage and share business application credentials amongst employees. With this feature, users can automatically capture and store credentials in the CyberArk secure vault. This feature also empowers users to share credentials and notes while controlling the ownership rules permissions to their resources.
BeyondTrust has a similar solution in Password Safe — a feature that ensures you have complete control and accountability over privileged accounts in your organization. The feature has a custom-defined approval technique for users’ access requests and authentications.
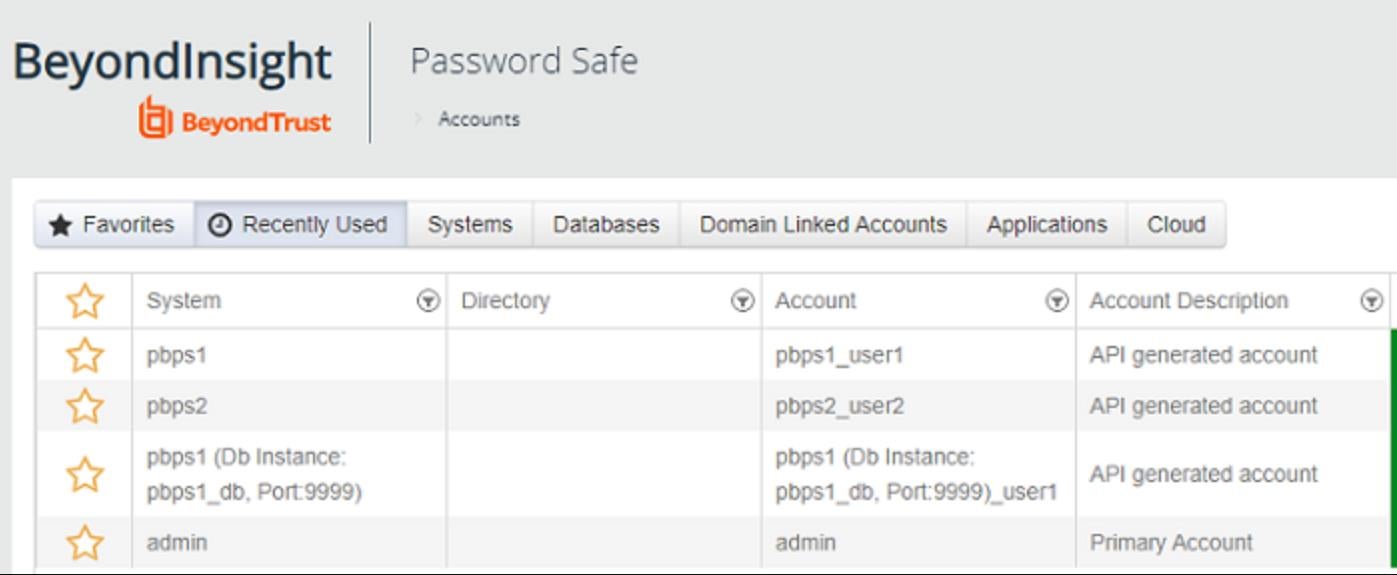
Privileged access management
CyberArk’s account-focused approach relies on privileged access management, account user behavior and account privileges. Through CyberArk’s Privileged Session Manager, businesses can secure, control and monitor privileged access to network devices.
In contrast, BeyondTrust is asset-focused, and the approach relies on environmental scanning to secure the organization’s digital assets. The platform supports remote access and offers agentless asset discovery to help organizations audit their systems and understand where vulnerabilities may exist. It also has an Endpoint Privilege Management solution that elevates privilege access to known, trusted applications that require them, controls application usage and logs and reports on privileged activities.
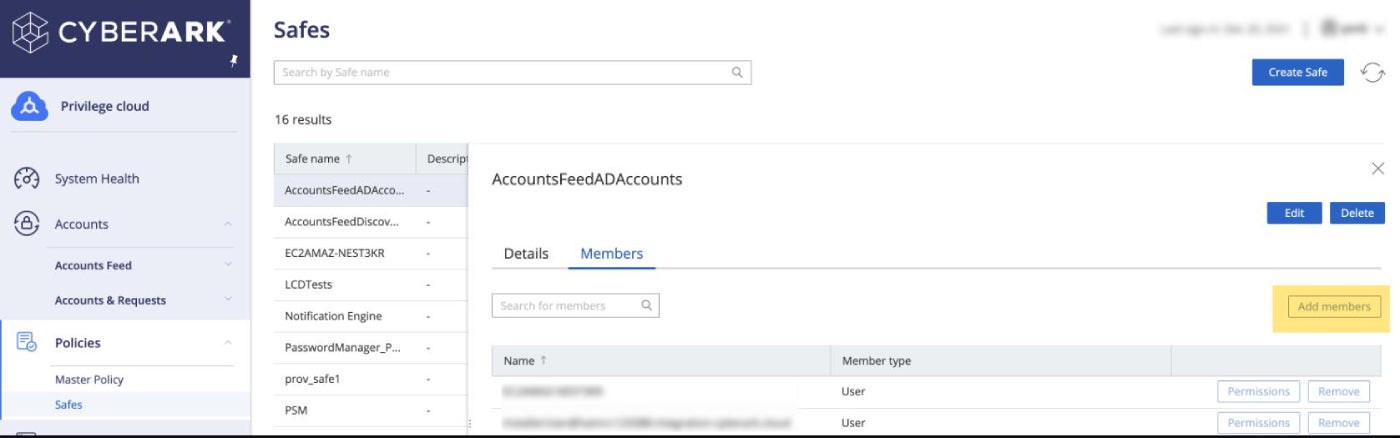
Simplicity and ease-of-use
For beginners, CyberArk has a substantial learning curve. Many small- to mid-sized organizations may find themselves hiring a professional to deploy the solution rather than deploying it internally. While documentation is available, it can be incomplete and inconsistent. A managed services provider may be needed for an organization to transition to CyberArk.
Comparatively, BeyondTrust’s solutions are fairly straightforward to use and deploy. BeyondTrust has a variety of features such as Smart Rules, Smart Groups and Direct Connect, all intended to make the overall user experience of BeyondTrust easier, thereby improving overall productivity.
Audience
Although CyberArk can theoretically manage up to 100,000 endpoints, the maximum implementation in the real world is 57,000. Nevertheless, CyberArk is more likely to be used by enterprise-level organizations, whereas BeyondTrust is more popular with small businesses and mid-market enterprises.
CyberArk’s features, functionality and complexity lend themselves better to an enterprise-level organization. Meanwhile, BeyondTrust’s simplicity, ease of use and painless deployment make it a better option for smaller companies and mid-sized organizations.
Interfaces
The features and functions provided through CyberArk’s web interface are not always the same functions that are provided elsewhere — potentially leading to confusion, especially in terms of API configuration.
BeyondTrust provides a clean, attractive interface, although some users find it lacking in more advanced features, such as group approval. While the BeyondTrust interface may not have as robust a feature set as CyberArk, it’s easier to use.
CyberArk pros and cons
While there are many advantages to using CyberArk for identity and access management, there are still some drawbacks to consider.
Pros of CyberArk
- Integrates very well with cloud-based and on-premise data centers.
- CyberArk vault is good for compliance needs.
- Allows privilege controls across the IT estate.
- Offers identity threat detection.
- CyberArk has a demo and free trial option.
Cons of CyberArk
- Can be complex to set up.
- The pricing model is complex. It requires a custom plan from the sales team.
BeyondTrust pros and cons
There are some advantages to using BeyondTrust. However, the platform does have its downsides too.
Pros of BeyondTrust
- It is easy to maintain and deploy.
- Has an identity-first security approach.
- Allows users to secure remote access to any infrastructure.
- Can detect and respond to security threats.
- Integrates well with technology vendors like AWS, SailPoint, Ping Identity, etc.
Cons of BeyondTrust
- Pricing is not well defined.
- BeyondTrust Remote Support costs can be pricey for small businesses.
Methodology
We assessed both CyberArk and BeyondTrust in terms of their IAM capabilities. During testing using the free trial available on both platforms, we took note of how key capabilities like threat detection, secret management and privileged access management work. We noticed that CyberArk’s features, functionality and complexity lend themselves better to an enterprise-level organization. Meanwhile, BeyondTrust’s simplicity, ease of use and painless deployment make it a better option for smaller companies and mid-sized organizations.
We supported our research by looking into user reviews and testimonials from Gartner to evaluate the performance of each solution in terms of user interface and overall user experience.
Should your organization use CyberArk or BeyondTrust?
CyberArk and BeyondTrust are fairly evenly matched IAM solutions that have a lot going for them. Today, BeyondTrust is one of the leading competitors in the field, but CyberArk is close behind.
Choose CyberArk if:
- You need a comprehensive IAM solution that can support on-premises, hybrid and cloud environments.
- You need an IAM solution with built-in privileged access management capabilities.
- You’re interested in an IAM solution that puts account management and account security first.
- You aren’t afraid of an IAM solution with complexity.
Choose BeyondTrust if:
- You need an IAM solution focusing on secure remote access and compliance with regulatory standards.
- You need an IAM solution with robust vulnerability assessment and patch management features.
- You’re interested in an IAM solution that puts asset management and asset security first.
- You need a solution fast and easy to deploy.
Ultimately, CyberArk and BeyondTrust are powerful IAM solutions that can help organizations manage their critical assets and protect against data breaches. When choosing between them, consider your organization’s needs, requirements and resources first.
This article has been updated from a previous version published on May 2, 2022; it was originally written by Jenna Inouye.


